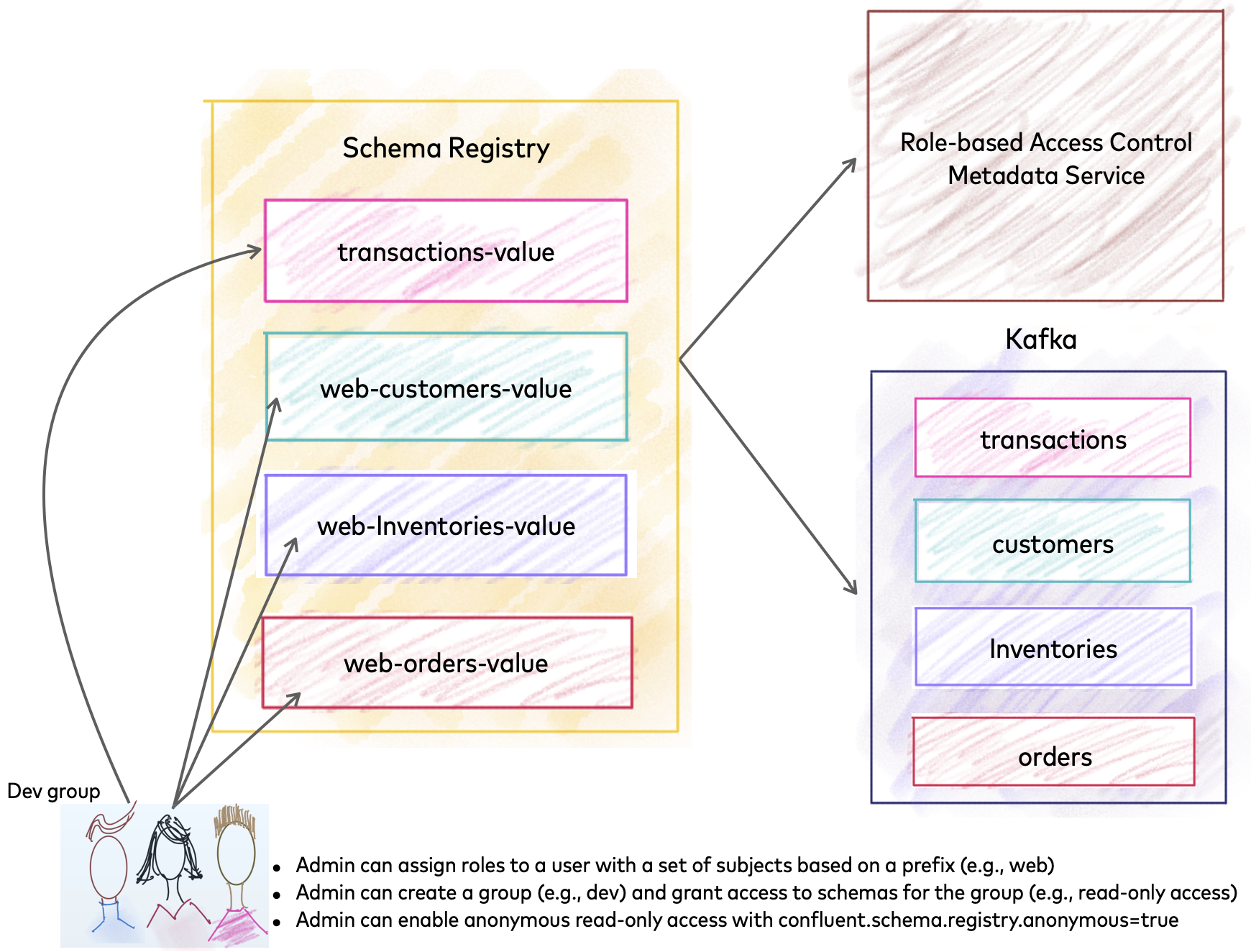
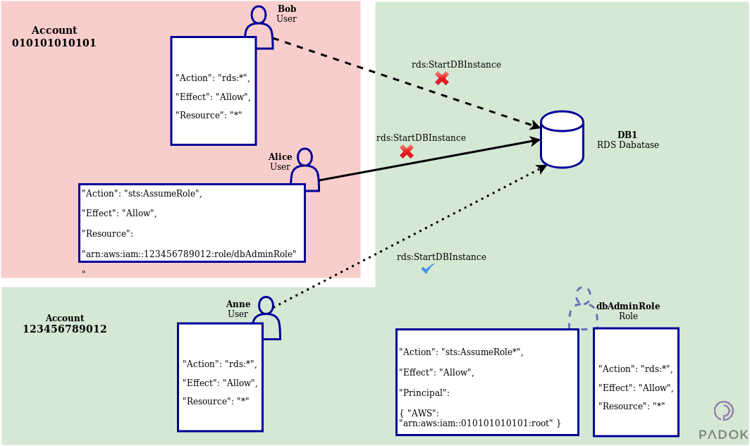
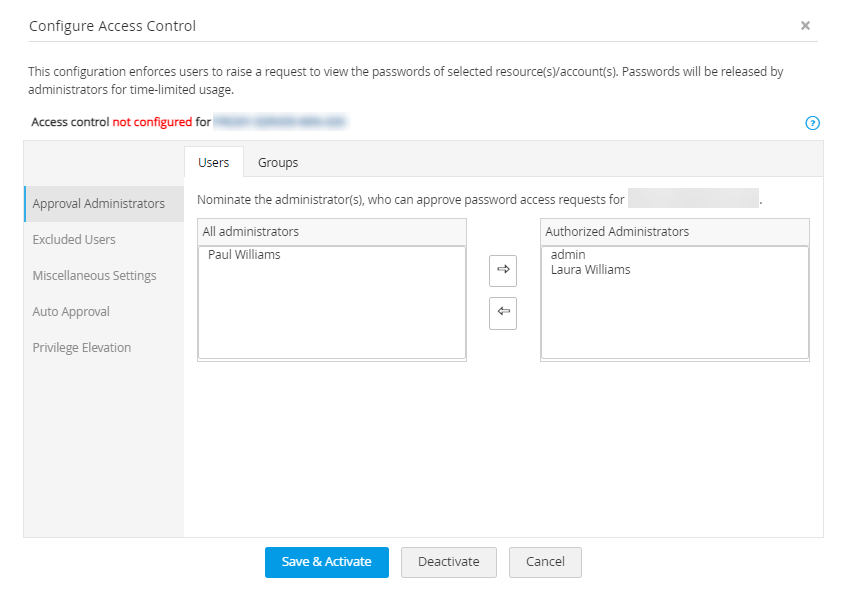
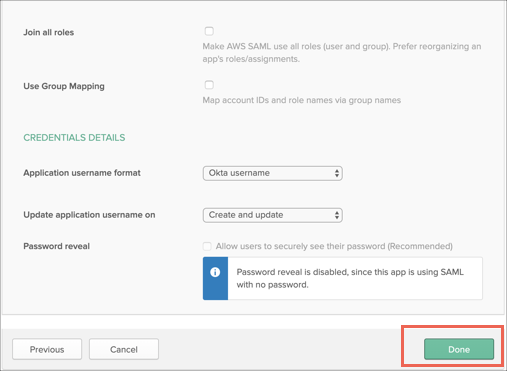
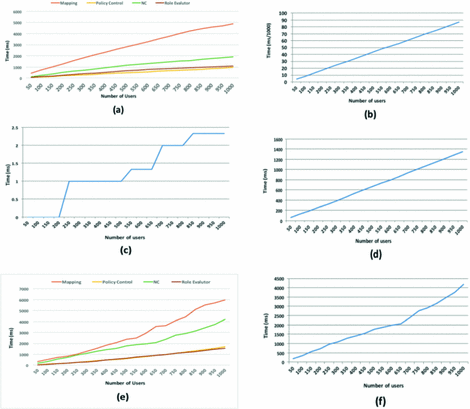
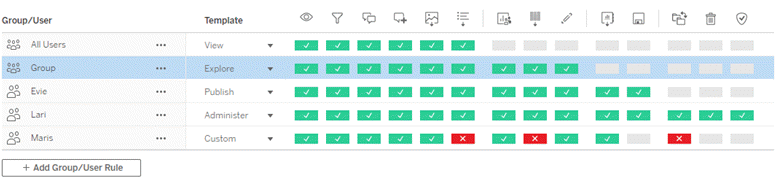
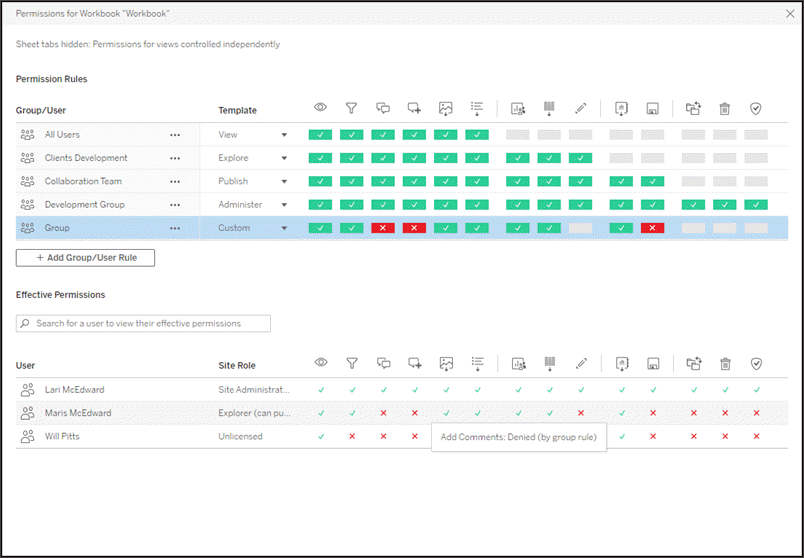
Implementing Role Based Security in a Web App | by Marcel Schoffelmeer | Bluecore Engineering | Medium

Amazon EKS with OIDC provider, IAM Roles for Kubernetes services accounts | by Marcin Cuber | Medium

How to use KMS and IAM to enable independent security controls for encrypted data in S3 | AWS Security Blog